Which Action Best Meets the Goals of Security
Identity and access management includes ensuring proper use of authentication measures authorization measures and privilege granting. A well-designed action plan can make it easier for you to track and realize your goals.

Marketing Is A Vital Action For Businesses Of All Sizes But What Is The Best Way To Market Your Bu Content Marketing Strategy Content Marketing Marketing
Through user-driven models and best practices we will deliver world-class customer- and user-friendly services and products.

. Promote the availability of data for authorized use. Successful authentication means preventing attackers from impersonating an authorized entity. Nolan is writing an after action.
Security architecture includes applying security best practices to the acquisition integration and operation of hardware and software. The level of detail in your action plan can vary based on the resources you have and the complexity of your project or goal. Protecting people developing expertise implementing cost reduction initiatives having the ability to provide proactive security following standard operating procedures the ability to audit and adequately training its.
What action best meets goal of security. Goals and Objectives of a Security Organization This paper will focus on major topics of a successful security organization. Even with the wide variety range all of the objectives and goals are basically the same from company to company.
Not security but stability is. Security Organization Goals and their Implementation The goals that must be achieved in security organizations are extensive. Maintaining a quality workforce is an important objective for a security company.
The real basic goals of information security are. The Interagency Security Committee ISC chaired by DHS consists of 54 Federal departments and agencies and has as its mission the development of security standards and best practices for nonmilitary Federal facilities in the United States. Accomplishing these is a management issue before its a technical one as they are.
Security management consists of nurturing a security-conscious organizational culture developing. Cybersecurity can be measured by at least one of three goals-. Governance is critical to accountability and allowing for an accurate view of risk for CEOs and other leaders.
Information security professionals who create policies. In this article we are going to study what these goals are that are to be met while ensuring data security. The security market has a wide variety of activities from physical to information security.
It describes the approach for resolving an issue that interferes with reaching company goals. Wearing a seatbelt in the car. The CIA triad is a security model that is designed to guide policies for information security within.
The person responsible for finding that balance and actively promoting organizational security is the security manager. Preserve the integrity of data. An important way that a security operation or company establishes Premium Management Security Computer security.
Strengthen alliances to defeat global terrorism and work to prevent attacks against us and our allies. Preserve the integrity of data. Businesses can have a far narrower range of goals and objectives because they do not have to deal with issues of national security.
CISOs must have a detailed framework for how security is handled yet it also must be adaptable to the changes that are inevitable due to regulations or new threats on the horizon. A corrective action plan is a documentation used in quality management that outlines a set of steps for addressing issues and gaps in business operations and processes that could negatively impact the business. Promote the availability of data for authorized users.
Champion aspirations for human dignity. What DLP technology would best meet this goal. Whether you have a career business or personal goal you can use an action plan to create a clear path to success.
Jades organization recently suffered a security breach that affected stored credit card data. Protect the confidentiality of data. This article is about the security goals which are the main aim and reason behind the cryptography.
Well-trained security personnel ensure that you can provide quality services to clients. These goals form the confidentiality integrity availability CIA triad the basis of all security programs see Figure 21. We will improve the performance and security of our IT business systems through integration and modernization and will identify enterprise solutions to reduce redundancies in core business platforms.
These goals form the confidentiality integrity availability CIA triad the basis of all security programs. Is security an economic goal. Computer security can be said to embody three general goals.
Regardless of your organizations specific goals and methodologies well-defined goals as well as upper-management endorsement will. Authentication The ability to reliably determine that data has been received as it was sent and to verify that the entity that sent the data is what it claims to be. The goals and objectives that a security organization must focus on in business and government operations are very similar the main difference being the scope of what must be focused on.
What reflects the goal of economic security. All information security measures try to address at least one of three goals. Submitted by Monika Sharma on January 09 2020.
The corrective action plan should be SM. Also we would be studying the principles of security. A security awareness program should be customized to meet the challenges and culture of your organization.
Jades primary concern is the fact that the organization is subject to sanctions for violating the provisions of the Payment Card industry Data security standard. Thus a key to successful security implementation is finding a reasonable balance between system protection and user autonomy and convenience. The first topic to be addressed is how each organization both within industry or within the governmental realm must ascertain their goals and recognize the consequences of failing to achieve their objectives.
Protect the confidentiality of data.

Super Kgb The Kgb Meets The Cia In 2 Spy Training Games Spy Training Arch Enemy Board Games

Professional Meeting Minutes Template In Pdf Word Meeting Agenda Template Meeting Notes Template Meeting Planner

Meeting Notes Template Meeting Notes Notes Template

Kick Off Meeting Agenda Meeting Agenda Template Meeting Agenda Agenda Template

How Can Accounting Erp Software Increase Security Accounting Software Human Resource Management

Meeting Notes Template Agenda Template Meeting Printable Etsy Meeting Notes Template Agenda Template Notes Template
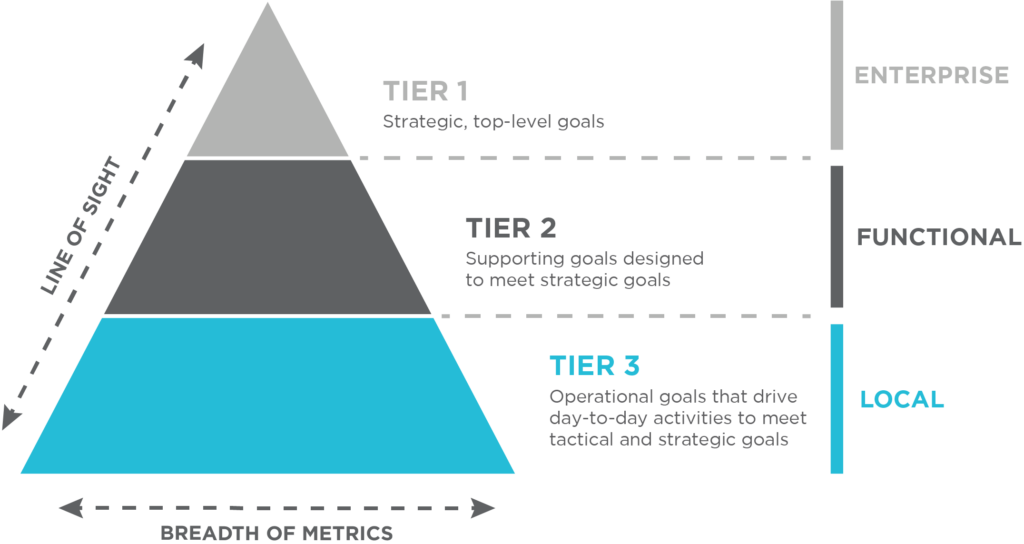
The Security Operating Model A Strategic Approach For Building A More Secure Organization Scottmadden

Are Cx And Service Design The Same Thing Service Design Customer Journey Mapping Customer Experience

Quality Management Infographic Project Management Professional Writing Rubric
0 Response to "Which Action Best Meets the Goals of Security"
Post a Comment